A Proactive Guide to the Nginx Check Config Command

We've all been there—that gut-wrenching moment when a tiny config change crashes a high-traffic site. For any sysadmin, that's the nightmare scenario. This is why validating your Nginx configuration isn't just a "best practice"; it's your first and most important line of defense against downtime, security holes, and sluggish performance. Think of the nginx -t command as your critical safety net before pushing any changes live.
Ready to build a more resilient server environment? Server Scheduler helps you automate routine tasks like reboots and resource scaling, minimizing manual errors and maximizing uptime. Explore Server Scheduler and start automating today!
Contents
Ready to Slash Your AWS Costs?
Stop paying for idle resources. Server Scheduler automatically turns off your non-production servers when you're not using them.
The Critical Role of Proactive Configuration Checks
Mistakes in Nginx configuration files are far more than minor typos; they can trigger major service disruptions and create serious security vulnerabilities. A single misplaced semicolon or an incorrect file path is all it takes to stop Nginx from reloading, effectively knocking your websites offline. Imagine making a routine update to an SSL certificate path. If you make a small typo, Nginx will fail to reload, leaving every site on that server completely inaccessible until someone hunts down and fixes the error. Running a quick nginx check config command would have caught that invalid path instantly, allowing you to correct it without a single second of service interruption. This preemptive check is absolutely essential, especially in complex setups with dozens of server blocks and include files.
 W3Techs.
W3Techs.
A proper Nginx check config process is the bedrock of reliable server management. It transforms a reactive, stressful "fix-it-when-it-breaks" approach into a proactive, predictable, and professional workflow.
This habit doesn't just protect your live environment; it gives you the confidence to make changes without fear. When you combine this practice with a solid disaster recovery plan, like a reliable strategy for backing up Linux systems, you're building a truly bulletproof infrastructure. Regular checks ensure every modification is deliberate and correct, forming the backbone of a stable and secure hosting environment.
Running Your First Nginx Configuration Test
Before you ever think about reloading Nginx with new changes, there’s one command that should be pure muscle memory: nginx -t. This is your safety net, your first line of defense against taking down your entire web server with a simple typo. Running this command kicks off a full syntax check of your Nginx configuration. It's not just looking at the main nginx.conf file; it dives deep, following every single include directive to pull in your virtual host files from sites-enabled or any other snippets you have in conf.d. It’s like Nginx building a complete map of your setup in memory and walking through every path to ensure it connects correctly, catching everything from a misplaced bracket to a forgotten semicolon.
![Computer screen displaying command to run nginx configuration test ></p>
<p>When everything is correct, the output is beautifully simple, giving you a clean confirmation that your syntax is valid. A successful <strong>nginx check config</strong> will look exactly like this: <code>nginx: the configuration file /etc/nginx/nginx.conf syntax is ok</code> and <code>nginx: configuration file /etc/nginx/nginx.conf test is successful</code>. However, when things go wrong, the output is even more useful. Instead of a cryptic error, Nginx tells you <em>exactly</em> what's wrong, right down to the file path and line number. This turns a potential needle-in-a-haystack debugging session into a quick fix. For example, a forgotten semicolon might produce an error like this: <code>nginx: [emerg] invalid number of arguments in](https://cdn.outrank.so/df605670-7321-4b7e-9064-2199881d28ad/37ef5828-60e4-49f8-96d1-7fa96362948d/nginx-check-config-terminal-command.jpg) . This pinpoints the problem to line 5 of a specific file, allowing for a swift correction.
. This pinpoints the problem to line 5 of a specific file, allowing for a swift correction.
Using Dry Runs for Deeper Configuration Insights
While nginx -t is your first line of defense against typos, it really only scratches the surface. It confirms your configuration is syntactically valid, but it won't tell you what your server will actually do when it loads all those nested include files and server blocks. For that, you need to go deeper. This is where the dry run command using the -T flag becomes your most trusted diagnostic tool. Unlike its simpler cousin, nginx -T first runs the same syntax check and, if it passes, then prints the entire, fully-assembled configuration right to your terminal. It resolves every single include directive and shows you the final config file exactly as Nginx will read it into memory. This is an absolute game-changer for debugging tricky issues in complex setups.
Imagine a specific location block isn't behaving correctly. Is the problem in that file, or is a conflicting directive from another file loaded earlier overriding it? Running nginx -T gives you a single, consolidated view of everything. You can pipe the output to a file or use a tool like grep to instantly find where a directive is being defined—or overwritten. It lays out the complete context, making it far easier to spot unintended inheritance or conflicting rules. This kind of deep inspection is a core part of effective test environment management best practices.
The -T flag transforms debugging from a game of hide-and-seek into a systematic process. It removes all ambiguity by showing you the final, definitive configuration that Nginx will use.
| Flag | Primary Function | Typical Use Case |
|---|---|---|
| -t | Performs a syntax check only. | The standard, everyday check before any reload to catch typos and basic errors. |
| -T | Performs a syntax check and then dumps the entire configuration. | Debugging complex setups, finding conflicting directives, or verifying include logic. |
| -c | Specifies an alternate configuration file to test. | Testing new or experimental config files in a safe location without touching live files. |
By mastering both the -t and -T flags, you're building a comprehensive toolkit to handle just about any Nginx configuration challenge, from simple syntax checks to the most complex debugging sessions.
Automating Nginx Config Checks in Your Workflow
Checking configs by hand is a good habit, but building real resilience means leaning into automation. When you weave the nginx -t command directly into your development and deployment workflows, you build an invisible safety net that catches bad configurations before they ever see a production server. It stops being a chore you have to remember and becomes a seamless part of your process. A solid strategy stacks different tests on top of each other, starting with a basic syntax check, moving to a dry run for a deeper look, and then a full view to see the final, compiled configuration.
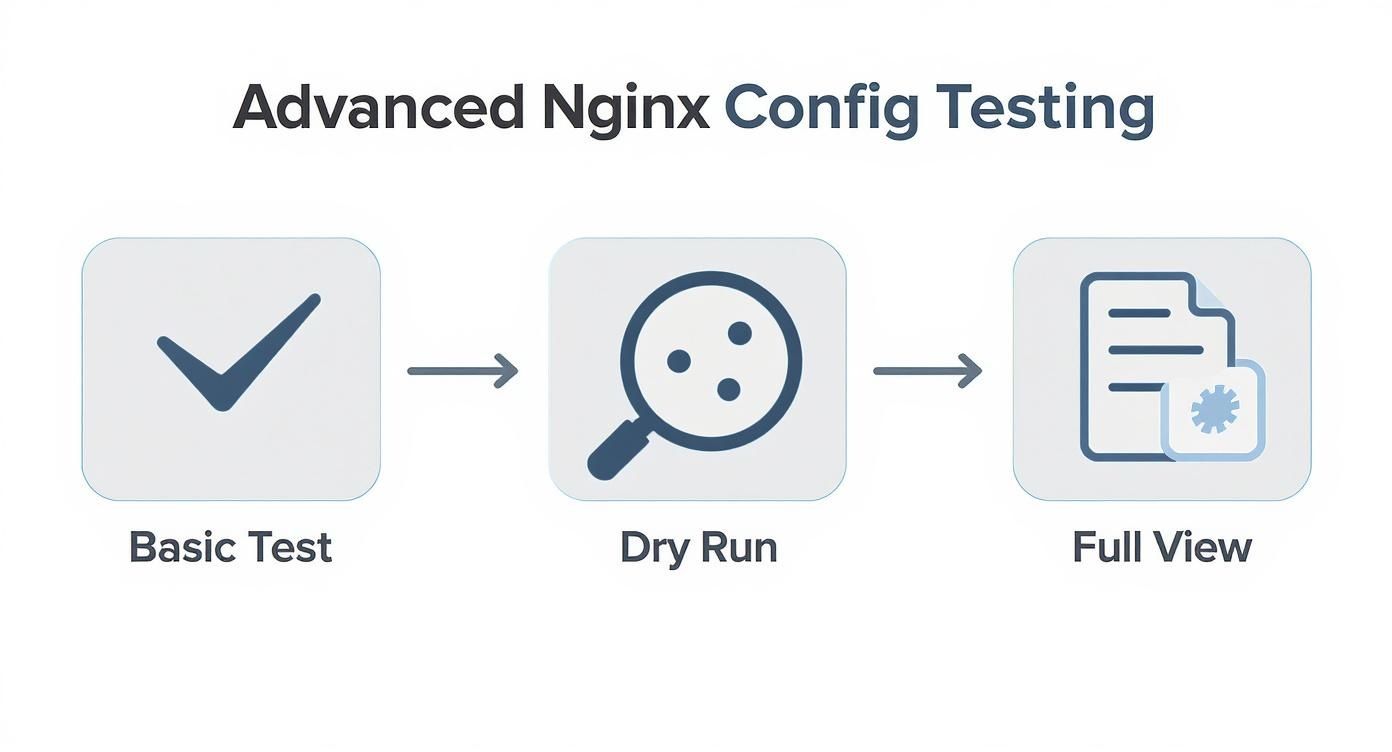
The best place to catch an error is on your local machine before it is shared. This is where Git hooks are perfect. You can set up a pre-commit hook to automatically run nginx -t on any .conf files you've staged. If the check fails, the commit is blocked, guaranteeing that no syntactically bogus Nginx files pollute your version control history. The next layer of defense is your CI/CD pipeline. You can add a dedicated stage that validates your Nginx config before any deployment kicks off. The pipeline halts if it fails, stopping a faulty configuration in its tracks. This is fundamental to understanding what DevOps automation is all about.
Decoding Common Nginx Configuration Errors
Even with the best testing process, some Nginx errors can be downright cryptic. Let's break down some of the most common issues that the Nginx configuration check flags to help build your diagnostic muscle memory.
An "unknown directive" message almost always points to a simple typo or a missing Nginx module. For example, using the gzip_static directive without the ngx_http_gzip_static_module compiled into Nginx will cause a failure. The fix isn't in your config but requires reinstalling or recompiling Nginx with the necessary module. Another common issue is the "invalid parameter" error, often seen in advanced setups like caching. Forgetting a required parameter like levels in a proxy_cache_path directive will trigger this error. The fix is as simple as adding the missing parameter back into the configuration line. Finally, permission errors are especially frustrating because your syntax can be perfect, but nginx -t still fails. A "(13: Permission denied)" message often relates to SSL certificates or log files that the Nginx worker process, running as a user like www-data, cannot access. The solution is to adjust file ownership (chown) or group permissions (chgrp) so Nginx can read the necessary files.
Frequently Asked Nginx Config Questions
As you get deeper into Nginx, certain questions pop up again and again. A common point of confusion is the difference between a reload and a restart. A restart (systemctl restart nginx) is a hard stop and start, dropping all active connections. A reload (systemctl reload nginx), on the other hand, is graceful. It starts new worker processes with the updated configuration and lets the old ones finish their current requests before shutting down, resulting in zero downtime.
Another frequent question is whether you can test just one server block. The direct answer is no, as nginx -t validates the entire configuration to check for inherited directives and conflicts. However, you can use the -c flag to point Nginx to a temporary file containing only the server block you want to inspect, effectively isolating it for debugging.
Finally, a classic frustration is when a reload fails even after nginx -t passes. A successful test only confirms correct syntax; it doesn't check for runtime issues. The most common culprit is permissions—the Nginx user might not have access to a new SSL certificate file. Another possibility is trying to bind to a port that's already in use. When a reload fails after a successful test, it almost always points to a deeper environmental problem, much like the process of learning how to find a memory leak in your system.